The Strategic Guide for Business Compliance with Bill 25

You are in charge of your company's IT security and are tasked with implementing Bill 25. You understand the crucial importance of this bill for strengthening your organization's cybersecurity. However, the mere idea of this task might seem overwhelming. How will you implement it effectively? What are the precise steps to follow? How can you be sure that you are in total compliance with the bill?
If you recognize yourself in this scenario, you are not alone. Many managers and leaders face similar challenges. They are often overwhelmed by the technical and legal details of the bill, unsure about the best way to apply it, and worried about the potential consequences of incorrect implementation. These challenges can breed a sense of insecurity, even vulnerability, in the face of the ever-increasing threat of cyberattacks.
We understand your concerns and desire to protect your business as best as possible. That's why, in this article, we will guide you step by step through a strategic action plan for implementing Bill 25. We will discuss key strategies, explain how to overcome common challenges and provide the tools for successful implementation.
[BLOG_POST_SUMMARY]
Key Strategies for Implementing Bill 25
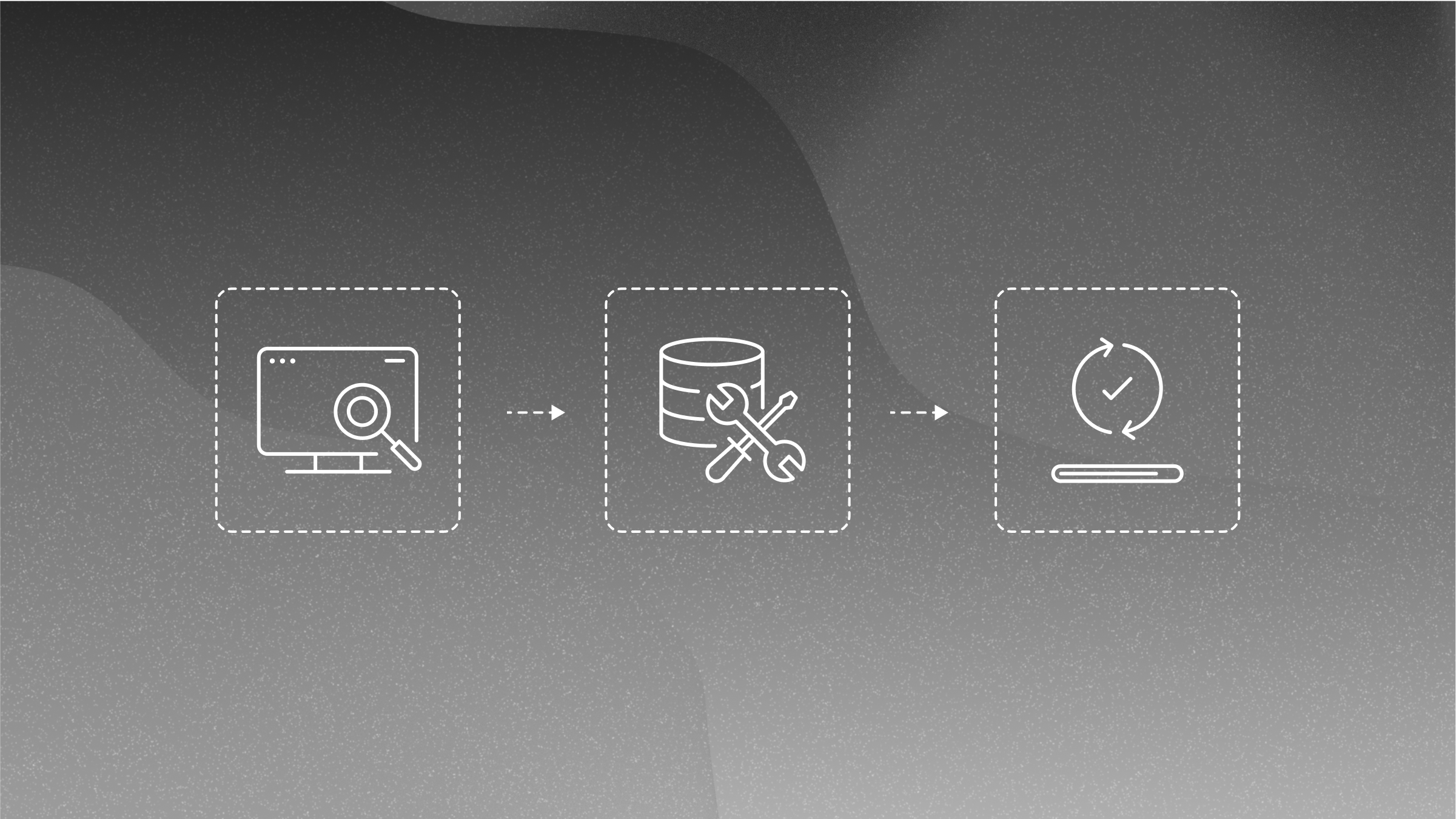
Given the growing importance of personal data security, compliance with Bill 25 has become necessary for all businesses. But how do you do it? Here's a three-step action plan to achieve this.
Risk and Vulnerability Assessment: The Starting Point
The first step to ensuring compliance with Bill 25 is to assess risks and vulnerabilities. But what does this mean concretely? It involves identifying and analyzing the risks that could threaten the security of your personal data. In this process, you review systems, policies, and procedures to find any loophole that malicious attackers could exploit.
For example, have you considered types of cyberattacks, internal errors, and external threats? The evaluation allows you to understand your system's weaknesses and set priorities. This precise knowledge of your vulnerabilities will help you develop a personalized and effective security strategy in line with the requirements of Bill 25.
Implementing Appropriate Security Measures: The Key to Success
Once risks are assessed, it's time to implement security measures. These measures must be robust and tailored to the nature of the data collected and the environment in which they are processed.
Do you think your IT security systems are up to date? Installing firewalls, intrusion detection and prevention systems, and VPNs to secure communications are examples of measures to consider. And let's not forget the physical aspect, with the secure storage of data.
You should keep in mind that 95% of cybersecurity breaches are the result of human errors. Have you already set up regular training for your staff? Developing clear data security policies and procedures, an incident response plan, the use of encryption for sensitive data and access control are all measures that will strengthen the protection of your personal information and help you comply with Bill 25.
Monitoring and Updating Protection Measures: A Continuous Effort
Threats, just like regulations, are constantly evolving. Therefore, it is essential to monitor and regularly update your protection measures. So, do you periodically review your security logs to detect suspicious activity? Do you carry out security audits and intrusion tests to verify the effectiveness of your security measures?
It is also essential to stay informed about the latest trends in cybersecurity. This will help identify new threats and best practices to deal with them. In addition, regular revision of your security policies and procedures is necessary to ensure their relevance and effectiveness.
In sum, compliance with Bill 25 is a continuous effort that requires constant vigilance and a willingness to improve continuously. Are you ready to meet this challenge to protect your most precious assets?
Remember, we are here to help you. At Genatec, we offer comprehensive cybersecurity solutions tailored to your business needs. Contact us now, and let's take the first step toward a safe and compliant digital future.
Challenges of Implementing Bill 25 and Their Solutions

Implementing Bill 25 can present several challenges. Let's look at potential challenges and ways to overcome them.
Limited Understanding of the Bill
Bill 25 is a complex document, and it can be challenging to understand precisely what it requires. This lack of understanding can lead to gaps in your compliance strategy, inadvertently exposing you to the risk of violation and costly penalties of Bill 25. To overcome this challenge, it may be helpful to consult with a lawyer or a consultant specializing in data protection who can help you understand the details of the bill and what it means for your business.
Modifying Existing Processes
You may need to modify some existing processes to comply with Bill 25. This can be difficult, mainly if these processes have existed for a long time. A step-by-step approach can be helpful here, starting with the most critical or urgent changes and gradually progressing.
Employee Awareness
All your employees must understand Bill 25 and how it affects their work. This can be a challenge, especially if you have a large team. To overcome this challenge, regular training and updates on the implementation of the bill may be necessary.
Costs of Compliance
Complying with Bill 25 can be expensive. You may need to invest in new technologies, training for your staff, or even hiring new employees to manage compliance. To address this challenge, a detailed budget is crucial. It might also be helpful to explore the possibilities of funding or grants available to help cover these costs.
Maintaining Long-Term Compliance
Once you comply with Bill 25, the challenge is to remain compliant. This may require regular monitoring and reviewing of your policies and procedures. To do this, consider appointing a compliance officer or establishing a dedicated team to ensure long-term compliance.
You might also like: 5 Common Mistakes Companies Make when Complying with Bill 25.
How Genatec Can Support You Throughout the Process
Bill 25 Compliance Services
Genatec offers a comprehensive suite of services to help you achieve compliance with Bill 25. We start by helping your leaders designate a Privacy Officer and post their contact information on your website. We will also explain the Privacy Officer's role and responsibilities by developing a precise and detailed job description and explaining its duties to the entire management team. Our service also includes personal data protection training for your management team, including how to respond to security incidents. In collaboration with the Privacy Officer, we will develop an incident response plan, where Genatec will be the first responder in case of a security incident.
We will also assist you in setting up an incident log in SharePoint, with all the incident details recorded in Genatec's ticketing system (ConnectWise). Preparing a communication plan to inform the Access to Information Commission and the affected individuals about any privacy incident presenting a severe risk of harm is also part of our services. Moreover, if your company uses biometric features or measures for identity verification or confirmation, we will assist you in preparing the necessary forms to submit to the Access to Information Commission.
Personal Data Governance Services
Regarding personal data governance, Genatec offers a detailed inventory of the applications and data processed in your company. We will also review access rights to applications that process personal data and help you understand and review the security of your software providers.
The development of security policies is another area in which we are experts. We will develop several security policies, including an information security policy, an acceptable use policy, data classification and labelling policy, and a data retention and destruction policy. In addition, we offer cybersecurity and personal data protection awareness training for your team.
Enhancement of Personal Data Protection Measures Services
Finally, our services for enhancing personal data protection measures include assistance in obtaining adequate cybersecurity insurance coverage. We will also implement measures to protect the confidentiality of data at rest and in transit.
Genatec also reinforces data access security by implementing password policies and multi-factor authentication. In addition, we will strengthen the protection and monitoring of workstations with tools such as MDM, EDR, RMM, and SIEM. We will ultimately assist you in setting up a Data Loss Prevention (DLP) solution to prevent data losses and breaches.
At Genatec, we are ready to support you at every step of your journey to compliance with Bill 25. Our team of experts is here to help you navigate this complex process and implement robust security measures to protect the personal data you process.
Wrapping Up

Personal data protection has become necessary in today's digital landscape. Bill 25, with its rigorous provisions, attests to the importance given to this issue in Quebec. As a result, companies must take proactive measures to ensure compliance. However, compliance with Bill 25 is not just a matter of law abidance but also a matter of trust and respect toward your customers and partners. Protecting their personal data demonstrates your commitment to their security and privacy.
At Genatec, we are determined to help you achieve and maintain compliance with Bill 25 while enhancing your company's cybersecurity. Thanks to our comprehensive range of services and deep expertise, we can guide you at every step of the process, from the designation of a Privacy Officer to the development of rigorous security policies and incident response plans. Moreover, our training and awareness services ensure that your entire team is informed and ready to act accordingly to protect personal data.
With Genatec by your side, you can rest assured that your personal information is effectively protected and that your business complies with Bill 25. We are committed to helping you safeguard your data, your reputation, and your future.
Contact us now to schedule a free consultation with one of our cybersecurity experts. Together, we can turn the challenges of Bill 25 into opportunities for improved cybersecurity and a safer digital future.
