6 Types of Cyber Attacks Your Business Should be Aware of in 2023

You're a business owner, and you keep hearing stories on the news about businesses getting hit by data breaches, ransomware infections, phishing scams, and other types of cyber attacks. It's scary and doesn't seem to get any better. It's time to take action and protect your business from cyber threats.
But you can't prevent what you can't understand. So The first step is understanding the types of threats that exist and what steps you can take to mitigate them. You might be shocked to learn that a single attack can be used multiple ways to gain unauthorized access or disrupt operations by taking advantage of vulnerabilities. By understanding the different methods and tactics that attackers use, you can better equip yourself with the knowledge to identify potential threats and create effective strategies for protecting your online security.
Many people find it challenging to learn about the different types of cyber-attacks because there is so much information. With all the acronyms and technical terms, it can seem overwhelming and difficult to understand. Additionally, with new attack methods constantly emerging, it's hard for individuals to stay on top of trends in the ever-evolving cybersecurity landscape.
We understand how complex it can be to try and stay up-to-date on the latest cyber security threats. But we're here to help. This article offers an overview of the most common types of cyber attacks and their definitions and examples.
@2x.png?width=2400&height=1350&name=Youre%20a%20business%20owner%2c%20and%20you%20keep%20hearing%20stories%20(...)@2x.png)
[BLOG_POST_SUMMARY]
Phishing attacks
What is a phishing attack?

A phishing attack uses social engineering techniques and exploits human behaviour to access confidential information or steal sensitive data from a victim's system, such as credit card information and passwords. Attackers typically send malicious emails, text messages, or phone calls to trick users into revealing sensitive information. Also, it's one of the most used techniques against businesses because it's easy to implement.
Since 2020, the number of phishing attacks reported to APWG has quintupled. Therefore, attackers sent over more than 1.2 million phishing attacks in the last quarter of 2022. As a result, organizations should be more aware of the variations of this kind of attack.
Email phishing
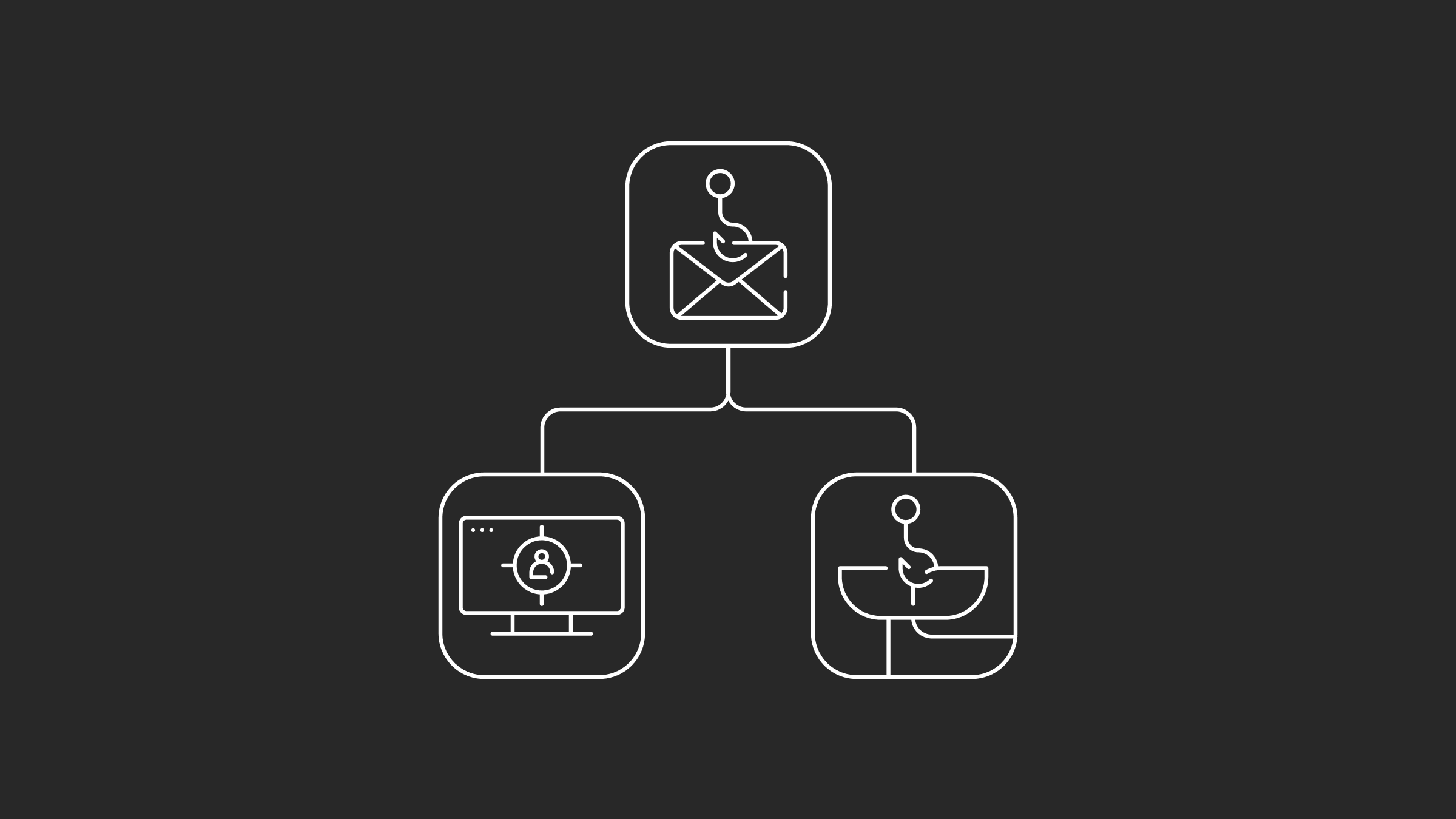
Nine out of 10 cyber-attacks start with an email. And there are two ways the attacker can do it. First, they can create a fake domain representing a legitimate organization, but some characters are substituted. Or they make an actual domain with the organization's name in the URL. And in both cases, the attackers send thousands of fake emails to victims with legitimate requests.
Spear phishing
Spear phishing attacks are when attackers target a specific person. To successfully execute this attack, the attacker will have some information, such as their name, job title, email address, place of employment, and information about their job role.
For example, the attacker can presume to be an employee from the finance department and write a convincing email to the victims requesting multiple legitimate service requests.
Whaling
A whale phishing attack is similar to spear phishing but more targeted. Let's take the same scenario, but the attacker acquired some executive's name and emails this time. They send it to a specific employee and tell him that they need an urgent bank transfer on behalf of the company. It gives the attacker more leverage and applies more pressure on the victim to do the required tasks.
Now that you know how easy it can be to trick one of your staff members, you are wondering how to detect and protect your business against it. Here are the measures and practices you can adopt in your business to prevent this kind of attack.
How to protect your business from phishing attacks

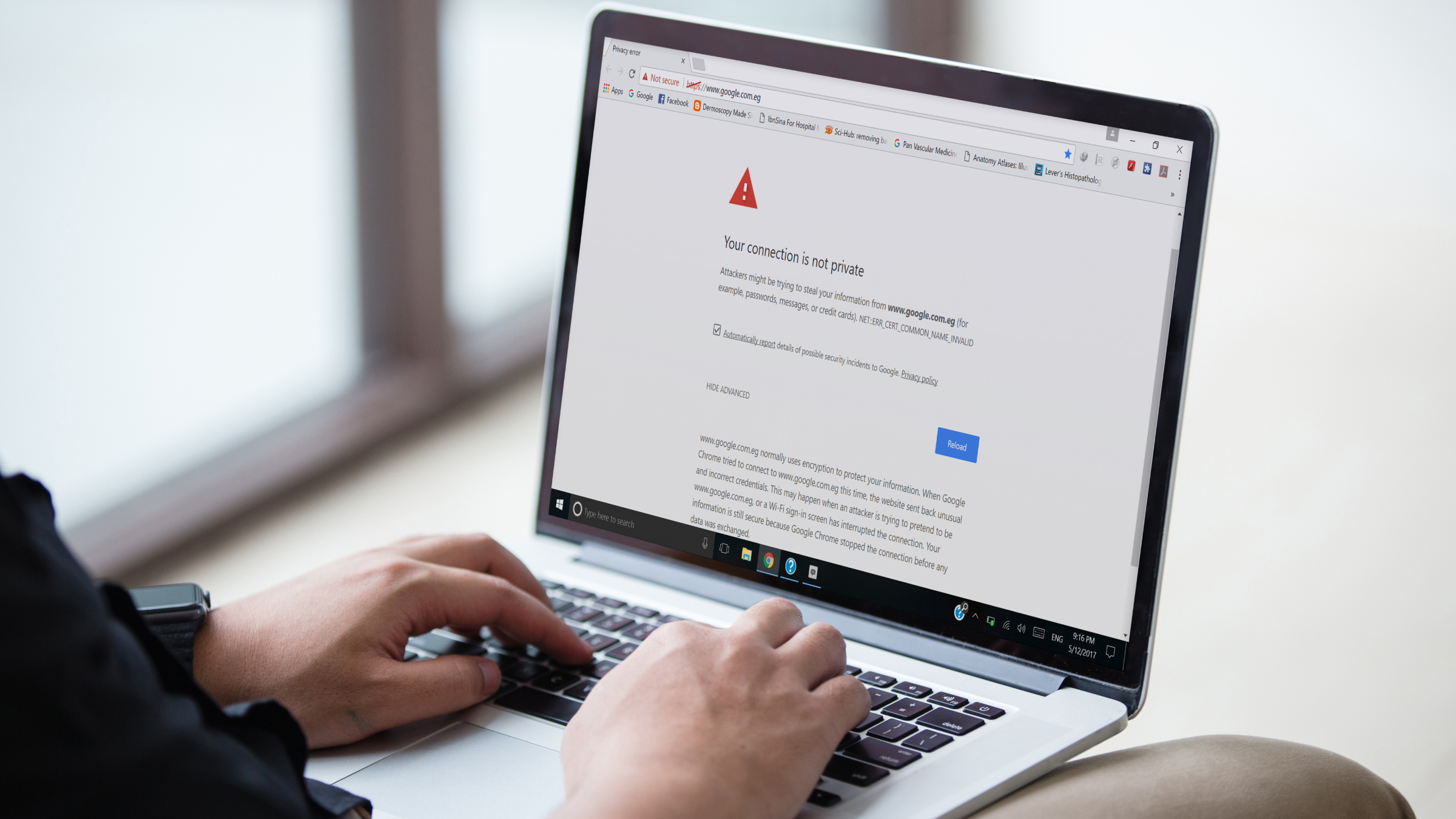
When you receive an email, you should always verify who sent you the message and what's the domain name. Sometimes it will be a random domain name, but it can look like something legit in most cases. In that case, always make sure to double-check with a member of the team and advise a supervisor. There will always be a link to click on or an attachment with it, and you should never click or open it. So whenever you see a suspicious email, your first reflex should be to flag it as 'phishing'. And if you want to take further action, it's better to report the incident to the support team for review.
Since 95% of cybersecurity breaches are caused by human error, the best way to prevent a phishing incident is to train your staff and implement awareness training against social engineering and phishing attacks. And people learn faster when they practice. So put in place a phishing campaign through the organization, and see how people react to it. In addition, take this opportunity to teach your staff the elements to look out for when they receive an email and to report them when it seems suspicious.
At Genatec, we offer cybersecurity training and awareness programs to help your team recognize phishing attacks and take the necessary steps to protect your data. Our phishing simulations help employees understand the risk of clicking on suspicious emails and guide them in navigating these potential threats.
Malware infections
What is a malware infection?

Malware attack is a term that refers to malicious software designed to gain unauthorized access and damage computer systems or infrastructure. Criminals can install malware for data theft, disruption of services, and other malicious activities to a target system. Malware infections are spread through various means, including email attachments, websites, downloads, or social media platforms.
Ransomware
Ransomware is a malicious virus that encrypts the victim's files and requires payment to unlock them. In most ransomware cases, attackers will demand payment in the form of cryptocurrency (Bitcoin, Ethereum). Still, there are also cases where they ask for cash or a bank transfer. Also, there are many ways for criminals to spread this malware in a network. The most popular one is via phishing email by sending malicious websites or an executable.
Ransomware is known to cause catastrophic damage to an organization. And since 2021, it has represented 21% of all cyber attacks. And it costs more than 20 billion dollars to the organizations.
Trojans
It's one of the oldest forms of malware. It is still commonly used by attackers due to its stealthiness and versatility.
This malware is a backdoor to computers and networks, allowing attackers to control and gather information remotely. And a backdoor is a malicious file or program hidden inside a legitimate file.
For example, attackers can hide malicious code inside a picture (PNG, JPEG). Then, the Trojan will execute the malicious code whenever this image is opened.
Virus and worms
A virus is malicious software replicating itself on a computer or network. Worms are similar to viruses but have some differences in behaviour. They don't require host files for execution because they replicate themselves via a vulnerable network (LAN) or Internet connection.
Also, worms intend to exploit specific vulnerabilities in computer or network operating systems. All these characteristics make them one of the most dangerous cyber threats.
Rootkits
Rootkits are malware that includes tools to exploit the system and grant an attacker access to the device or network. It's hard for antivirus products to detect these infections because rootkits hide deep in the design, making them almost invisible.
Rootkits also change legitimate files on the system and modify core components such as registries and drivers. Removing them without damaging the infected computer or network makes it difficult.
Malware breaches can be scary due to multiple variations and behaviour. But don't worry! Here are the best measures and actions to avoid being a victim.
How to protect your business from malware infections

Unless it is a ransomware attack, other types of malware can be pretty subtle when it infects a device. Here are some elements you can verify.
Files or applications can hide some malware. So, you should run a scanner to see if there are unknown files in the device or if there has been a modified file. Also, you can check the logs and see if a suspicious command has been executed from a corporate machine. Suppose a device starts to experience slow performance or odd behaviour. In that case, you'll need to disconnect the infected systems and investigate for further analysis.
Antivirus and anti-malware programs are essential for any organization to protect itself from malicious code, ransomware, and other malware attacks. Also, those programs actively scan the device to ensure that all files and programs are clean. They prevent and block any abnormal behaviour. Always keep the devices and software updated to avoid attackers exploiting a vulnerability.
Additionally, organizations should back up all data regularly to recover quickly in case of a malware infection or other cyber attacks. It will help ensure that no data is lost and that operations can resume as soon as possible.
Genatec provides various ransomware protection solutions that can detect and block malicious activities. We also offer backup solutions to help you recover from an attack in the event of data loss and disruption. Contact us today to learn more about how our security services can help protect your business from cyber threats.
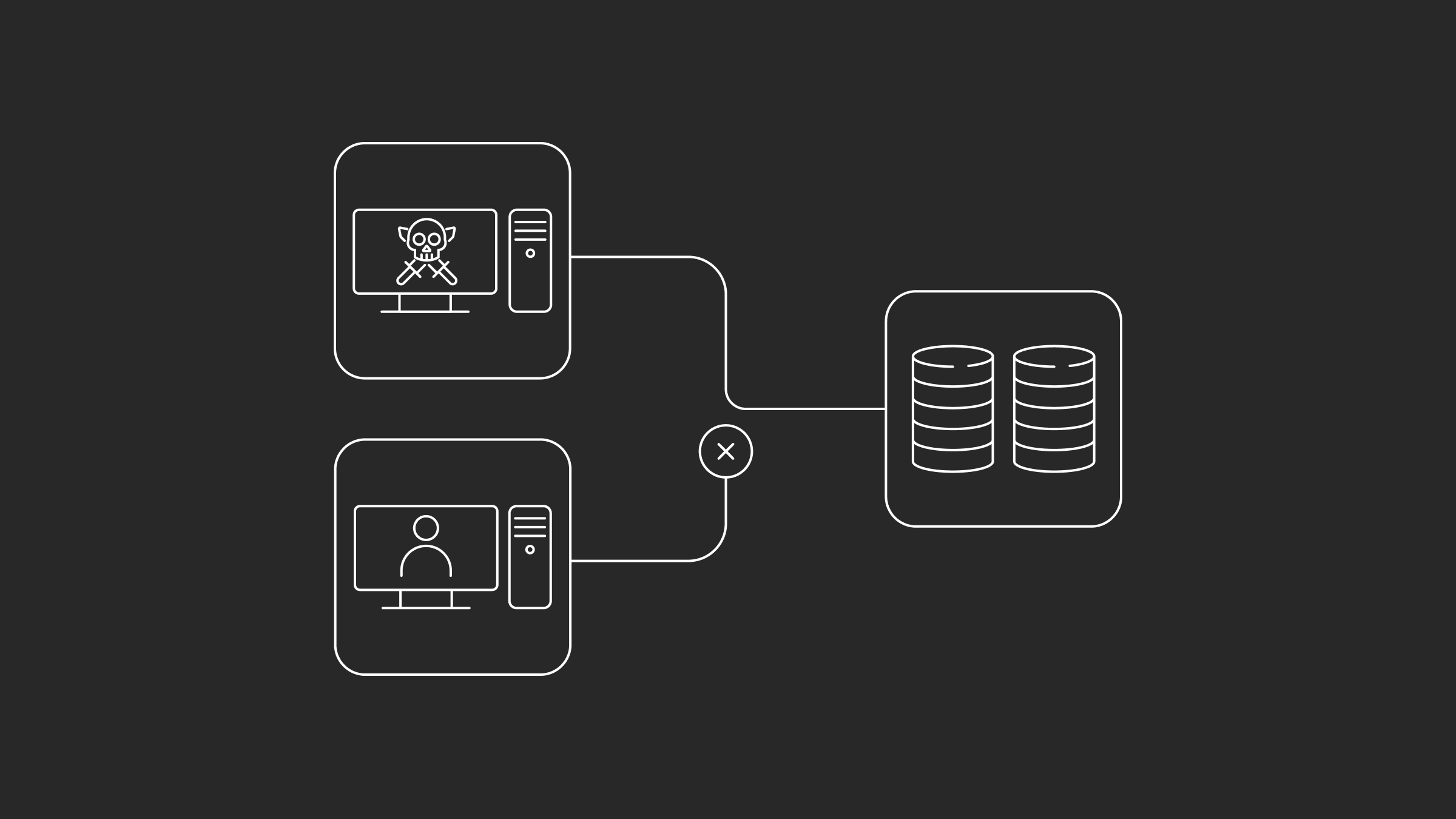
Unauthorized access
What is an unauthorized access attack?
Unauthorized access is an attack that takes advantage of the weaknesses of multiple computer network systems or a network vulnerability, granting malicious actors access to the data and resources. Therefore, after gaining access, they can steal confidential data or execute more cyber attacks, such as ransomware attacks.
This attack is commonly executed by exploiting vulnerabilities in systems or applications. However, social engineering attacks or brute-force attacks can do it too.
Brute force attacks consist of trying different combinations of characters until the hacker finds a valid username/password combination. To make those password attacks effective, attackers will either take a standard password list found on the Internet or get a list of thousands of breached passwords.
81% of company data breaches are due to poor passwords. So a great way to avoid being a victim of a brute-force attack is to use strong passwords. They must contain eight characters long and include uppercase and lowercase letters, numbers, and special symbols.
How to protect your business from unauthorized access attacks
With a monitoring system, such as an Intrusion Detection System (IDS), you can trace the incoming connections inside a network or critical infrastructure. It also allows you to detect an abnormal pattern and know if an external agent is trying to get access to any asset in the organization. This system lets the organization see and act quickly when suspicious activity occurs. It is also essential to keep track of any new applications installed, which could potentially put the whole environment at risk if not adequately evaluated by experts.
To better enhance your organization's protection from this attack, firewalls are an essential security measure for any organization. They monitor and filter traffic to block unauthorized access and malicious activities and protect sensitive data. Furthermore, configuring a DMZ (Demilitarized Zone) is also recommended. It is a secure network between the internal and external networks in which services are hosted to protect the internal network from external threats. In addition, a virtual private network (VPN) is an excellent protection because it adds a layer of protection to limit access and communication from outside.
Organizations should also implement multi-factor authentication whenever possible for an extra layer of security to their systems. Applications like Microsoft Authenticator require users to input a second factor, such as an access code sent via text message or email, before they can gain access to the system. This method helps to authenticate the user and make sure that it is the right person who makes the request.
You may also like: The Importance of Cybersecurity: 15 Tips to Secure Your Business
Denial of Service Attacks
What is a denial of service attack?
A denial of service attack, commonly known as DOS, consists of flooding a network with fake requests to shut it down. This attack can target a system, disrupt a complete service, and seriously affect business operations, leading to financial losses. It is one of the most potent cyber attacks that criminals still use today due to its efficiency. And here’s how they do it.
To leverage this attack, attackers use botnets to create a distributed denial-of-service attack or DDoS. A botnet is a collection of computers known as "zombies" infected by malware and controlled remotely by a criminal. And with a simple command, they can send thousands of malicious requests to a network and, in a matter of seconds, can shut down any services.
Here is a common scenario for this attack.
You own a small online store and have recently noticed that your website has been experiencing intermittent slowdowns. You worry that you might be the victim of a DDoS attack.
You look at the logs and notice that your website receives unusually high requests from unknown IP addresses. You check your server's resources and see that it is almost at capacity, despite there being no visitors to the website. You suspect that the requests are coming from malicious bots.
But there's no need to worry. This attack is not stealthy, and here is how you can build your defence.
How to protect your business from a denial of service attack
Detecting this kind of attack is straightforward. You will start to notice many unusual requests to a server on your monitoring system. Some devices or parts of the network will begin to experience demanding performances. Also, it might cause some services of your business to be wholly unreachable and unavailable. Denial of service attack can cause difficulties with communication and completing tasks.
An Access Control List (ACL) is an essential security measure against denial-of-service attacks. It specifies which users or systems can access specific resources within an organization's IT infrastructure.
Data Breaches
What is a data breach?

Data breaches occur when an unauthorized person gains access to confidential data or resources. Attackers can also leverage social engineering tactics to get people to reveal sensitive information or get login credentials.
Once the attackers gain access to a system, they can steal data such as credit card numbers and Social Security numbers. They can then use this information for identity theft or financial fraud.
The above scenario can also be possible from the other side. An attacker can pretend to be someone, get access to its credentials, and use it to execute a data breach.
A data breach can be costly if it strikes an organization. In 2022, the global average data breach cost was 4.4 million dollars.
How to protect your business from a data breach
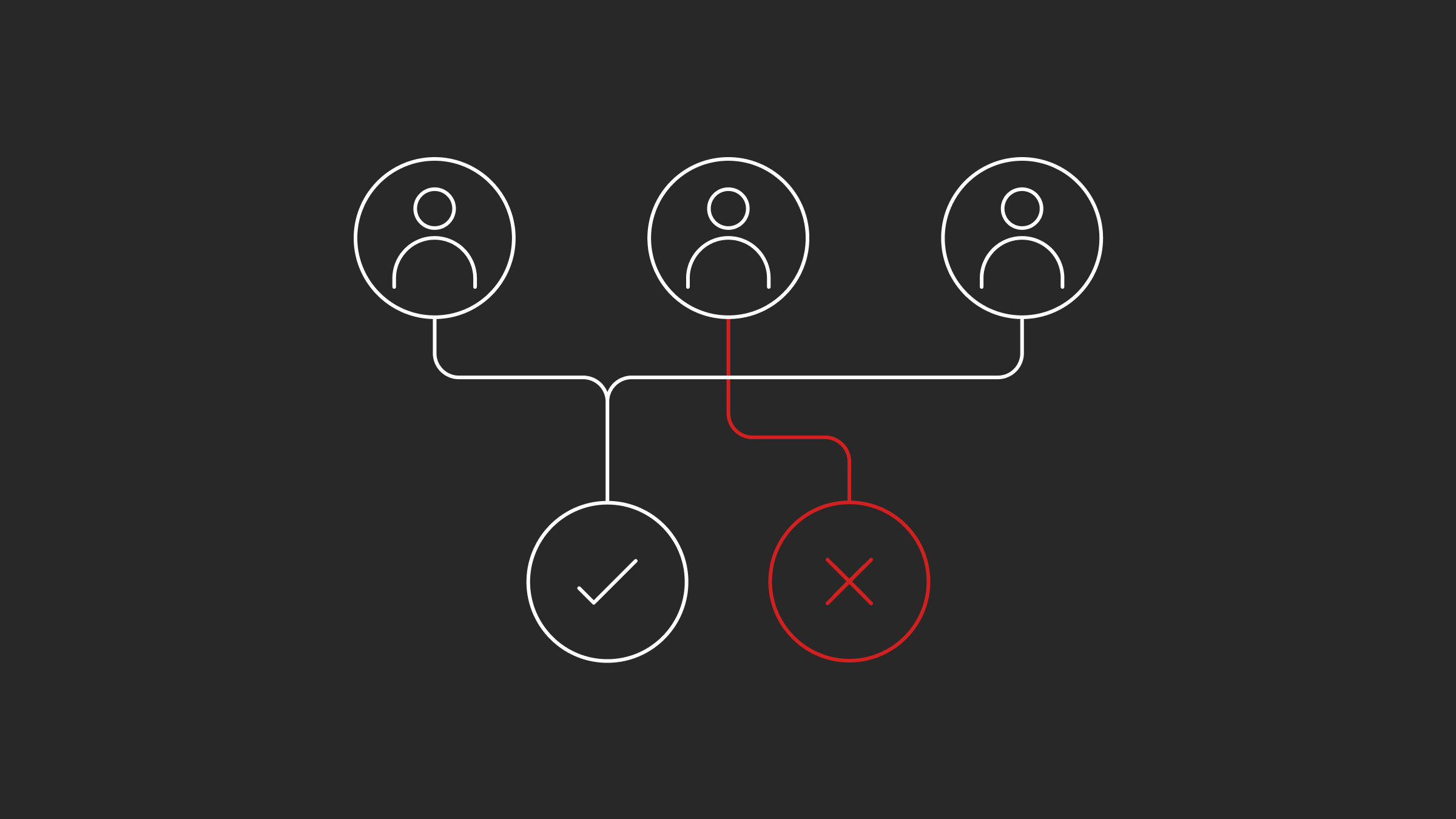
Detecting a data breach or identity theft can be challenging. Indeed, it can take more than 200 days for an organization to notice it.
To detect this kind of attack efficiently, organizations should have a monitoring system that triggers an alarm if a significant amount of data is being transferred or moved. Also, an unrecognized connection from an unknown device can indicate that credentials could have been compromised and be aware of any suspicious transfer or asset access. Being proactive in detecting a data breach can improve the response.
Role Access Base Control (RABC) is an essential security measure that helps organizations protect their data from identity theft. It allows you to define user roles to grant or deny certain privileges to users based on their job duties.
Moreover, organizations should also encrypt their data, both at rest and in transit. This crucial security measure helps protect the organization from external threats by preventing malicious actors from tampering with or accessing the data without authorization. In addition, classifying the information that circulates in different networks can help organizations react proactively if an unwanted transfer is taking part.
Insider Threat
What is an insider threat?

Insider threats are a type of cyber attack executed by someone within the organization, an insider. These attacks can be intentional or unintentional and can cause severe damage to an organization's assets and reputation.
The malicious insider can be an employee, contractor, or business partner. The attacker might have access to confidential data and the ability to modify systems or networks unauthorizedly.
For example, an employee who gets fired or is ill-intentioned can perform harmful actions that affect a business, such as leaking confidential data or stealing intellectual property.
Organizations affected by this type of attack spend an average of 15.4 million dollars. It's an increase of 34% since 2020.
How to protect your business from an insider threat

This attack can occur in many ways. A log system can help detect and trace all the connections done by the organization's staff. Therefore, all systems and services should have it in place. Also, an Intrusion Detection System (IDS) adds a layer of protection as it can detect abnormal behaviour.
It's essential to take note that an insider threat can happen in a physical environment. A surveillance system in specific places, such as a server room, can help detect any abnormal activity.
In addition, background checks are an essential security measure for any organization. They help protect against the potential risk of insider threats and provide a more comprehensive view of a person's past. Background checks include searching criminal records, verifying employment history, and checking academic qualifications.
Furthermore, organizations should regularly review access privileges within their IT infrastructure. By removing unnecessary user access, organizations can mitigate the risk of insider threats and reduce the potential damage caused by malicious actors.
At Genatec, we understand the importance of protecting your business' data with top-notch security solutions. Our cybersecurity solutions include firewalls, anti-malware software, two-factor authentication tools and 24/7 monitoring services to protect your systems from potential cyber-attacks. Contact us today to learn more about our solutions and services.
Wrapping Up

Cyber threats are an ever-growing concern for businesses. But with the right knowledge and strategy in place, it is possible to protect your business from these malicious attacks.
By understanding the different types of cyber-attacks, their methods and tactics, and the steps you can take to mitigate them, you can help keep your business safe from potential threats. And by staying informed about cyber security trends and investing in safeguards such as firewalls, anti-malware software, and two-factor authentication, you can make sure that your business’s online security remains in top shape. Storing and backing up data will help ensure that operations can resume quickly in case of a breach.
With the right understanding and proactive measures in place, you can protect your business from cyber threats. Don't let cyber criminals win. Start taking action today to ensure the safety of your business and its data.
Still don't know where to start? Genatec is here to help you protect your business from cyber threats. Contact us today to learn more about our security solutions, and let us help you stay safe from cybercriminals.
