The Importance of Cybersecurity: 15 Tips to Secure Your Business

We've all been victims of cyberattack attempts. It can be an unusual transaction on your credit card, an urgent email from your "friend" requesting money, or a call from someone pretending to be your internet provider. Being a victim of cyberattacks is stressful and makes you feel vulnerable and unsafe.
Now, imagine if these situations were to happen to you on a business level. Imagine if your entire network is the target of a cyber-attack. This is the reality of businesses nowadays.
It's becoming harder to detect cyber threats as criminals develop sophisticated tactics to steal your data. And addressing these threats appropriately is not only the responsibility of your cyber security team. Every employee plays a lead role in protecting your company.
Are your employees up to the task? And are they up to date on the latest cyber security best practices? Whether it's phishing, malware or ransomware, your team should always be on the alert and ready to respond to such threats. That's why resilience and business continuity should always be at the forefront of your cyber security strategy.
But the challenge business owners face is not knowing where to start regarding cyber security. It can be daunting, especially if you're unfamiliar with the technical jargon. But don't worry, we're here to help. We understand how challenging it is to keep up with the latest cyber security threats and best practices. That's why we've gathered a list of the most important aspects you need to know about cyber security for your business.
In this article, we'll look at the importance of cyber security for businesses and the impact of cyber security breaches and offer 15 tips that will help you avoid being the next victim.
[BLOG_POST_SUMMARY]
What is cyber security?
In today's digital age, businesses are increasingly reliant on technology. We use computers and the internet for everything from storing sensitive data to communicating with customers and employees. This reliance on technology makes businesses more vulnerable to cyber-attacks.
Cyber security: Definition
Cyber security is the process of protecting electronic information by mitigating information risks and vulnerabilities. These risks can include unauthorized access, use, disclosure, interception, or destruction of data. And data can include the confidential information of businesses or individual users.
Cyber security covers a wide range of activities, including:
- Access control: It allows you to ensure that only authorized users can have access to systems, data, and resources.
- Identity and authentication: They help you verify the user's identity and devices before granting them access to systems, data, and resources.
- Data security: It protects data from unauthorized use, access disclosure, interception, or destruction.
- Incident response: It allows you to identify, contain, and eradicate cyber threats.
- Risk management: It is the process of assessing, identifying, and prioritizing risks to organizational assets, systems, and data.
Cybersecurity threats include viruses, malware, ransomware, phishing scams, and denial-of-service attacks. These threats can destroy businesses, causing data breaches, financial losses, and reputational damage.
Types of cybersecurity measures
Companies can take different types of cyber security measures to protect themselves from cyber-attacks. Some of the most common actions include:
- Preventative measures: They are designed to prevent cyber-attacks from occurring in the first place. These measures include installing firewalls, encryption, and creating strong passwords.
- Detective measures: They allow you to detect cyber-attacks after they have happened. Examples of detective measures include activity logging, intrusion detection systems, and malware scanning.
- Corrective measures: They correct the damage caused by a cyber-attack. This includes data backups, disaster recovery plans, and patch management.
- Recovery measures: They help you recover from a cyber-attack. Examples of recovery measures include incident response plans and business continuity plans.
You may also like: How to Get Started with IT for Small Business: A Complete Guide.
Why is cybersecurity important?
Cybersecurity is important because it protects your business from cyber-attacks. And cyber-attack can have devastating consequences on your company, causing data breaches, financial losses, and reputational damage. In some cases, a cyber-attack can even lead to the shutdown of a business.
Why invest in cybersecurity
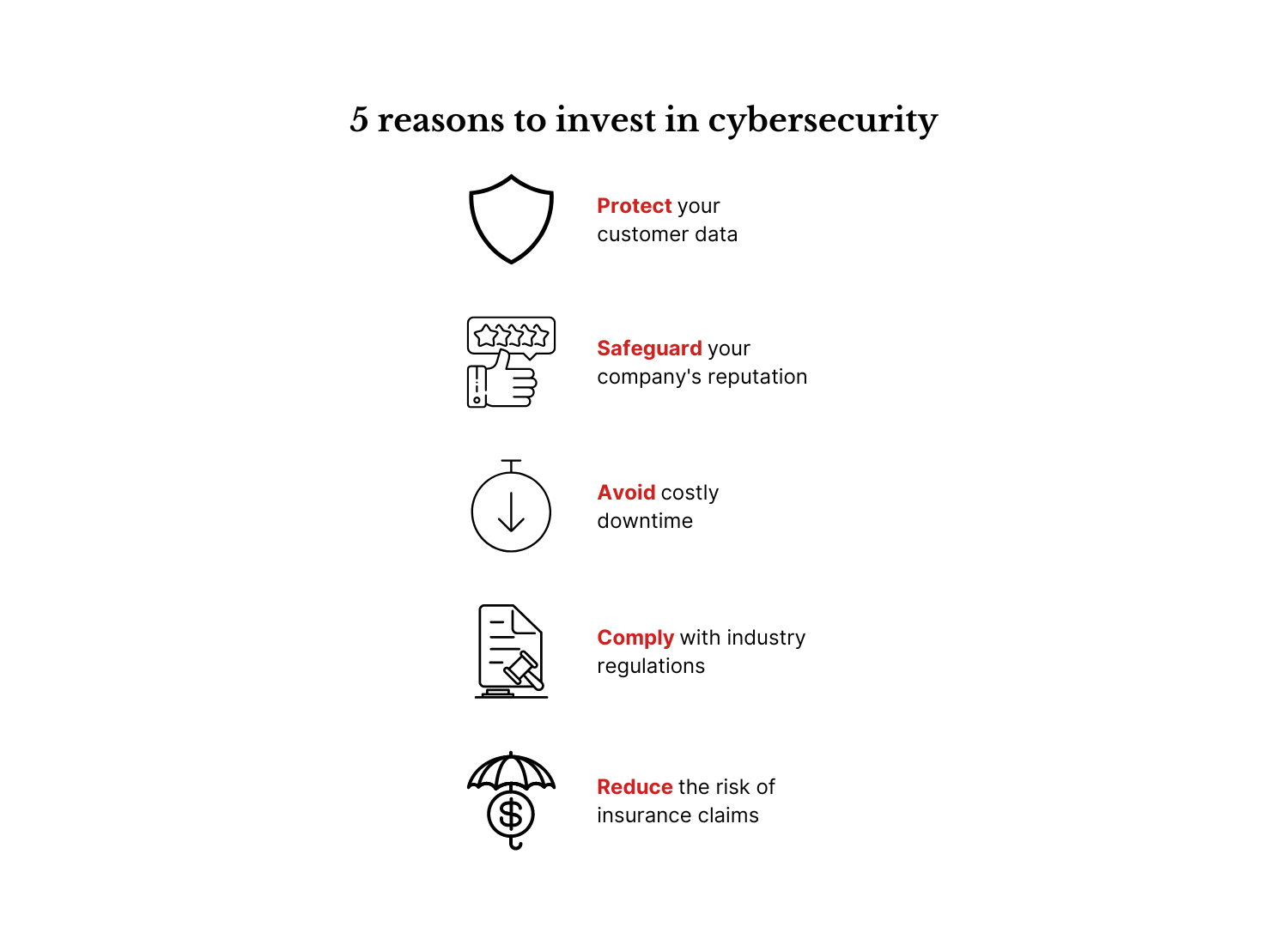
In the past few years, we have observed an increase in cyber attacks, with companies of all sizes becoming targets. While some businesses can recover from these attacks, others are not so lucky and go out of business.
That's why your company should invest in cyber security. Cyber security allows you to:
- Protect your customer data: Customer data is one of the most valuable data of any business. If this data ends up in the wrong hands, it can be used to commit crimes such as identity theft and fraud.
- Safeguard your company's reputation: A cyberattack can damage your reputation, even if you can quickly recover from the attack.
- Avoid costly downtime: Downtime can be expensive, especially if it results in lost sales or productivity.
- Comply with industry regulations: Many industries require businesses to protect their data, such as the Payment Card Industry Data Security Standard for companies that accept credit cards.
- Reduce the risk of insurance claims: Some insurers may refuse to pay out on a claim if they believe the business could have prevented the loss if it had adequate cyber security measures.
Implementing a great cybersecurity strategy can be complex and expensive, but the costs of not doing so can be even higher. By taking steps to protect your business, you can help to avoid the potentially devastating impacts of a cyberattack.
The benefits of a great cybersecurity strategy

Your business should have a cybersecurity strategy to help protect it from cyber-attacks. This strategy should meet your business's specific needs and consider the type of data you hold, how it's used, and the threats you face.
A great cybersecurity strategy will:
- Help you to understand the risks that your business faces: By understanding the risks that your business faces, you can make informed decisions about the measures that you need to put in place.
- Allow you to allocate resources effectively: Not all businesses have the same cybersecurity needs, so it is essential to allocate your resources to meet your specific requirements.
- Help you respond quickly to incidents: A well-designed cybersecurity strategy will help you respond rapidly and effectively to incidents, minimizing the damage they can cause.
- Enable you to recover from an incident: A good cybersecurity strategy will include measures that will help you recover from an incident, such as data backups and disaster recovery plans.
- Improve your overall security: By taking a holistic approach to cybersecurity, you can improve the general security of your business.
You may also like: 6 Types of Cyber Attacks Your Business Should be Aware of in 2023
The consequences of cyberattacks

Cyberattacks happen every 39 seconds. And the risks are becoming more and more detrimental and can have negative consequences for businesses. Cybersecurity is essential for any business but vital for small businesses. 43% of cyberattacks are directed towards small businesses as they are often seen as easy targets by cybercriminals and have fewer resources to dedicate to cybersecurity. And 60% of small businesses go out of business after a cyberattack.
The costs of cyberattacks

There are various ways that poor cybersecurity can hurt your business. Here are 5 of the most costly cyberattacks:
Data breaches
Data breaches are one of the most significant cybersecurity risks businesses face today. A data breach occurs when confidential, sensitive, or personal data is accessed without authorization. This happens when hackers gain access to your company's systems or employees accidentally leave data exposed. The average cost of a data breach is $4.35 million.
Ransomware attacks
Ransomware is malware that encrypts a user's files and demands money to decrypt them. Ransomware attacks are becoming increasingly common and can be incredibly costly for businesses. The average cost of a ransomware attack is $4.54 million, and the average cost of a destructive attack is $5.12 million.
Phishing attacks
Phishing is a cyberattack that uses fraudulent emails or websites to trick users into giving sensitive information, such as login credentials or financial information. Phishing attacks are often used to steal data or infect systems with malware. And 86% of companies claimed to have at least one user connecting to a phishing site. The average cost of a phishing attack is $4.91 million.
Denial of service attacks
A denial of service (DOS) attack is a type of cyberattack that attempts to make a system or network unavailable to its users. DOS attacks achieve this by flooding the target with requests and overwhelming its resources, preventing it from answering legitimate requests. The average cost of a DOS attack is $2 million.
Insider threats
An insider threat is a type of cyber threat from within an organization. Insider threats can occur when employees or contractors have malicious intent or when they accidentally expose sensitive data. Insider threats can be very costly in terms of the direct damage they cause and the indirect costs associated with them. The average cost of an insider threat is $4.18 million.
The risks of poor cybersecurity measures

In addition to financial costs, cyberattacks may lead to indirect costs such as lost productivity, customer churn, and reputational damage. Other risks include:
Loss of customer trust
87% of customers said they wouldn't buy from a company if they didn't trust the company to protect their data. A data breach can damage your reputation and make it difficult to win new prospects. Customers are increasingly conscious of the importance of cybersecurity, and they will not do business with companies that cannot protect their data.
Legal liability
If a business is a data breach victim, it may be liable for the damages. In some cases, companies may also be held responsible for negligence if they fail to take adequate security measures.
Regulatory penalties
Businesses that suffer data breaches may be subject to regulatory penalties. For example, the Personal Information Protection and Electronic Documents Act (PIPEDA) requires companies to take security actions to protect customer information. If a business fails to do so, it could be fined up to $100,000.
Reputational damage
If a business suffers a data breach, its reputation may be damaged. This damage can result in lost customers, revenue, and increased regulatory scrutiny.
Competitive disadvantage
A data breach can lead to lost business opportunities. Customers may prefer to do business with companies with better security, and investors may be hesitant to invest in companies at risk of data breaches.
You may also like: 8 Tips for Transitioning to a Managed Service Provider
15 tips to improve your cybersecurity
As the number of cyberattacks increases, it is becoming more critical than ever for businesses to have a robust cybersecurity strategy. A good cybersecurity strategy will help to protect your business from cyberattacks, and it will also help you to recover quickly if your business is attacked.
Cybersecurity best practices
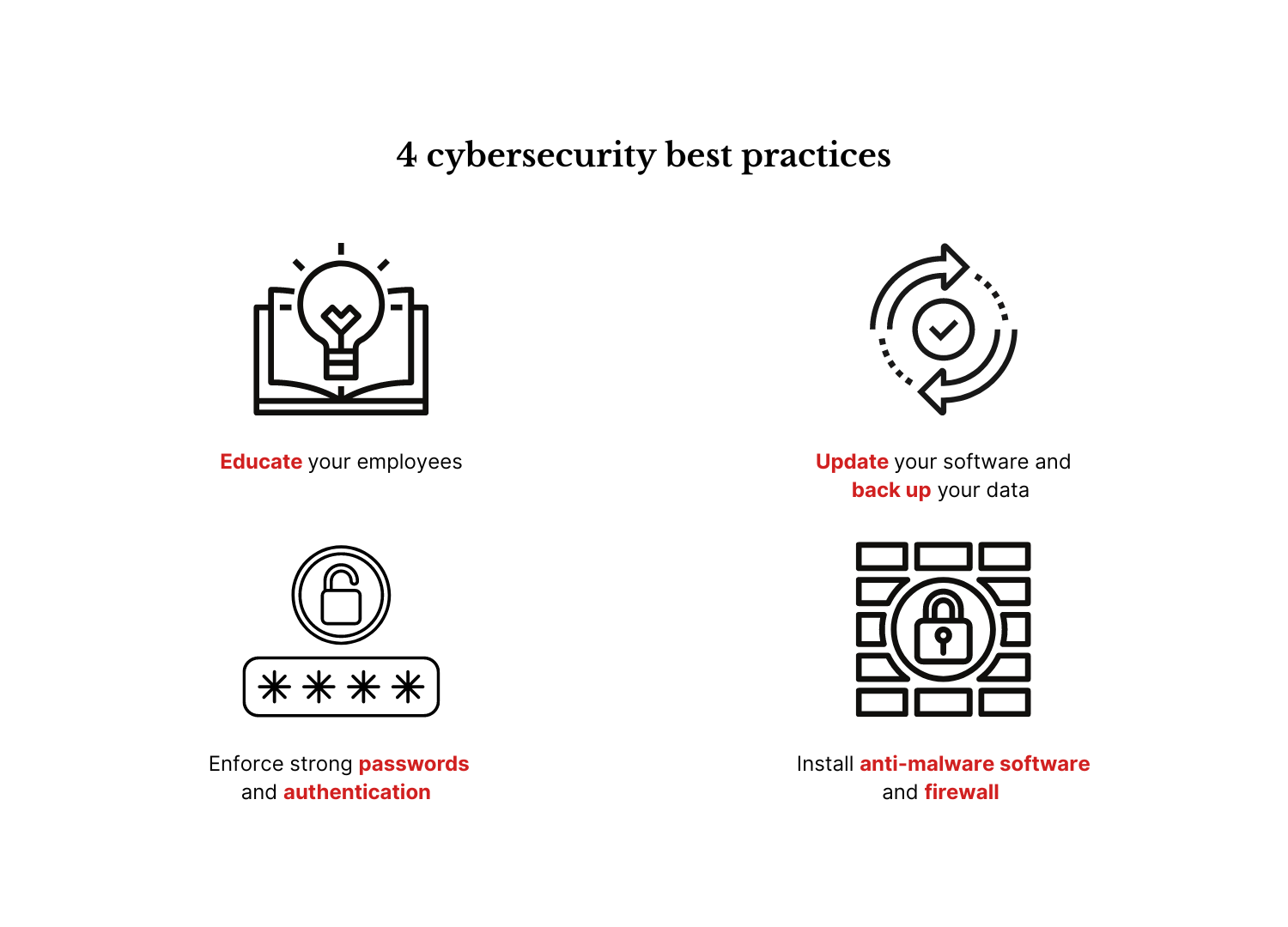
Educate your employees
Cybercriminals will penetrate your business through your weakest link. And the weakest link in your company is its people. Since 95% of cybersecurity breaches are caused by human error, you must constantly educate your employees on cybersecurity risks, policies and practices. It's not a one-time training but an ongoing process that evolves. Attackers are constantly developing new creative ways to hack companies. So, getting regular updates on new protocols and policies is crucial.
At Genatec, we offer customized training sessions for your company to meet your business goals and requirements. We deliver ongoing training and support to ensure a continuous and growth-oriented learning process. These sessions will help you understand your human cyber risk. You will get to keep an eye on your employees' security practices. And you will monitor and improve the overall cyber awareness of your company.
Update your software and back up your sensitive data
One of the easiest methods to detect and fix vulnerabilities is by keeping your software up to date with the latest protection programs. These programs are frequently updated to adapt to the newest cyber threats. So, by updating your software, you're also making your IT infrastructure more robust and resilient to attacks.
Since cyberattacks frequently target your data, it's crucial to always back it up. This will help your business get back on track in a cyberattack. Your data can be backed up on an external hard drive, in the cloud, and even offline. They can also be stored in any other secure location that's not accessible to attackers.
Install antivirus software and firewall
The reality is that even with the best training, your employees might click on something they're not supposed to. And with just one click, they end up downloading malware and putting your network security at risk. You should install antivirus software to prevent this malware from penetrating your network.
In addition, you should also use a firewall. It acts as a barrier between your data and cybercriminals. And its primary purpose is to monitor and filter incoming and outgoing traffic and keep secure traffic in and dangerous traffic out.
Enforce strong passwords and authentication
Using simple passwords is like handing attackers a key to your systems. Unique, strong, complex passwords will stop them from accessing your data. And you should use different passwords for your accounts. You won't have to worry about forgetting your passwords if you use a password management tool like LastPass.
Multi-factor authenticators are also crucial for businesses. Applications like Azure Active Directory provide an additional layer of protection. They force users to always confirm their identities before using their accounts.
Now that you know the importance of cybersecurity for businesses, it's time to put these tips into practice through a robust cybersecurity strategy.
How to create a robust cybersecurity strategy
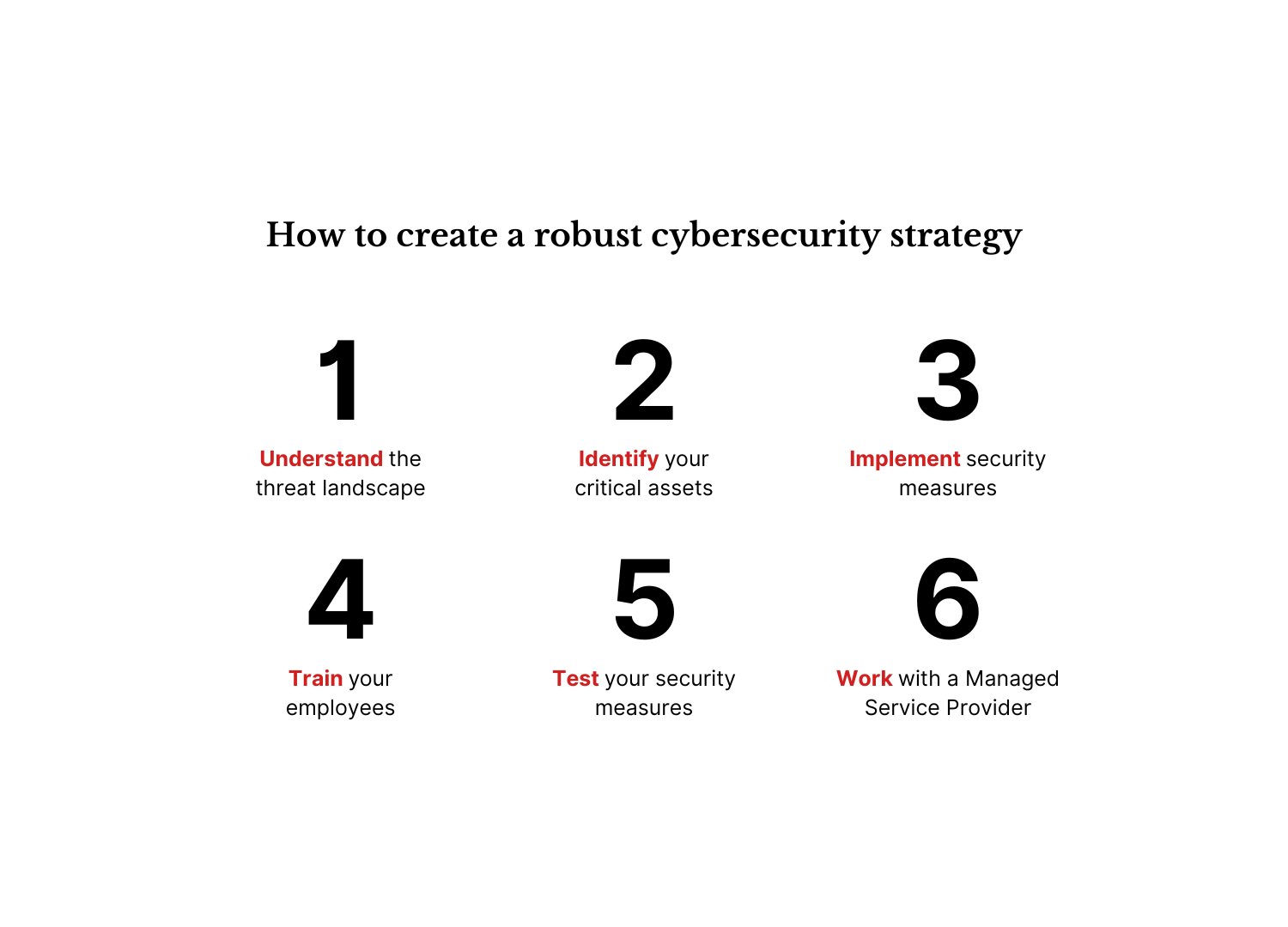
Understand the threat landscape
Understanding the threat landscape is the first step to developing a solid cybersecurity strategy. What types of attacks are common in your industry? What are the motives of attackers? How have other businesses been attacked? Understanding the threat landscape allows you to tailor your security measures to your business's specific risks.
Identify your critical assets
The next step is to identify your critical assets. What are the most important data and systems for your business? What would be the impact of losing access to these assets? By identifying your critical assets, you can ensure they are adequately protected.
Implement security measures
Once you have identified your critical assets, you must implement security measures to protect them. There are many different security measures, and the specific actions you need will depend on your business and the attacks you are most at risk of. However, some of the most common security measures include firewalls, intrusion detection and prevention systems, anti-virus software, and encryption.
Train your staff
Your employees are one of your most significant assets – but they can also be your biggest security risks. Employees may accidentally click on a phishing email or download malware from the internet. So to reduce these risks, it is essential to train your employees in cybersecurity. They should know how to spot a phishing email, how to keep their passwords safe, and what to do if they think their computer has been infected with malware.
Test your security measures
Once you have implemented security measures, it is crucial to test them regularly. There are many security tests, but some of the most common include vulnerability scans and penetration tests. By testing your security measures, you can ensure that they are effective and identify any weaknesses that need to be addressed.
Work with a Managed Services Provider
Working with a Managed Services Provider (MSP) is a great way to improve your cybersecurity. MSPs are cybersecurity experts and can help you implement the best security measures for your business. When you outsource your cybersecurity to an MSP, they can monitor your systems 24/7 and respond quickly to security threats.
At Genatec, we don't believe in one-size-fits-all strategies. Through our IT consulting services, we analyze your technology needs so you can get answers tailored to your business requirements. We plan, develop and implement your solution and continuously monitor your IT infrastructure. We provide you with the latest cybersecurity technologies that will not only deliver comprehensive protection to your business but also give you a business edge.
What to do after a cybersecurity incident
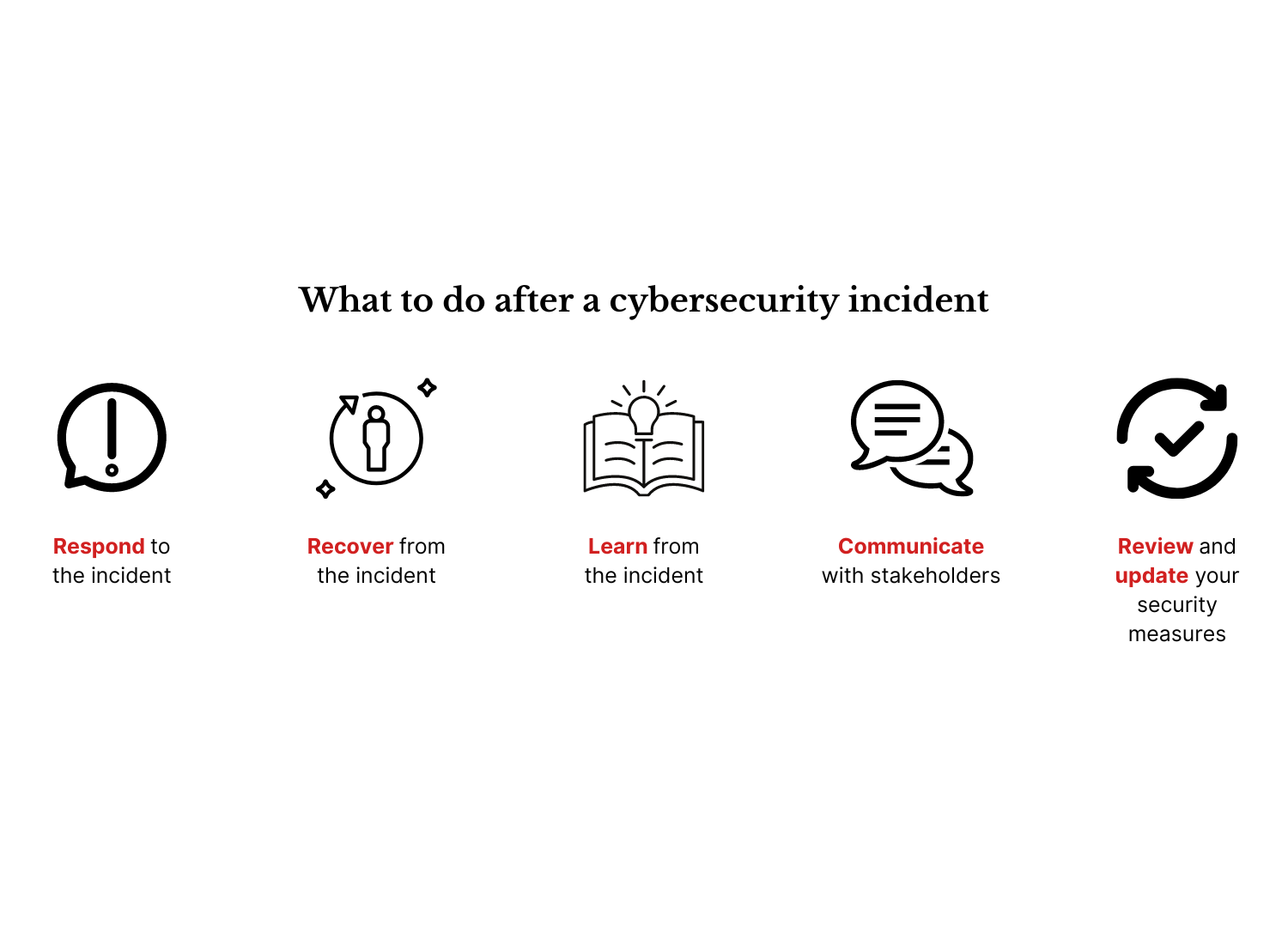
Respond to the incident
Despite your best efforts, a cybersecurity incident is always possible. If this happens, it is crucial to have a plan to respond to the incident. This plan should include steps for containing the damage, recovering lost data, and communicating with customers and other stakeholders.
Recover from the incident
After an incident has been contained, your business will need to focus on recovery. This may involve restoring lost data, repairing damaged systems, and updating security measures. Recovery can be a long and daunting process, but getting your business back up and running as swiftly as possible is essential.
Learn from the incident
After an incident, it is essential to take the time to learn from what happened. What went wrong? How could the incident have been prevented? What can be done to improve your security measures? Learning from incidents can strengthen your cybersecurity strategy and prevent future attacks.
Communicate with stakeholders
Communication is essential after a cyberattack. You must communicate with customers, employees, shareholders, and other stakeholders. It is necessary to be transparent and honest about what happened and what is being done to prevent similar incidents in the future.
Review and update your security measures
The final step in developing a strong cybersecurity strategy is regularly reviewing and updating your security measures. Your security measures will need to evolve as the threat landscape evolves. Regularly reviewing and updating your security measures can ensure your business is always protected.
Wrapping up
Cyber-attacks are one of those things you never expect to happen to you until they do. And no matter how big or small your business is, it might be the next target of a cyber attack. Cybercriminals are becoming savvier and are constantly developing new strategies to hack companies and extort money.
So taking measures to protect your business can reduce the risk of being attacked and minimize the damage if an attack occurs. To effectively protect your business, you must implement security measures, train your employees, and regularly test your security. In the event of a cyber attack, it is vital to have a plan to respond and recover. Finally, you should learn from incidents and regularly update your security measures to keep up with the fluctuating threat landscape.
With advanced training and a robust strategy, you can build a security shield that protects your business from cyberattacks.
Still trying to figure out where to start? We'd be more than happy to help you with your cybersecurity needs. Our IT experts will assess your requirements and tailor the perfect solution for your business. Claim your free audit to get started!
